To create programmatic Access Keys for an AWS IAM User using AWS CLI, run the command aws iam create-access-key.
On the command below change MyUser with the username of your target IAM User.
aws iam create-access-key --user-name MyUserThis will return the following JSON formatted string.
{
"AccessKey": {
"UserName": "MyUser",
"AccessKeyId": "AKIAV2JIEQKTMD4WNGFL",
"Status": "Active",
"SecretAccessKey": "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",
"CreateDate": "2022-06-20T06:44:30+00:00"
}
}Note the AccessKeyId and the SecretAccessKey. These are the details that you need to access your AWS Account programmatically via AWS CLI and AWS SDK.
This is the only time you will see the SecretAccessKey so be sure to note this.
The AccessKeyId is a unique identifier that you can see in your IAM user.
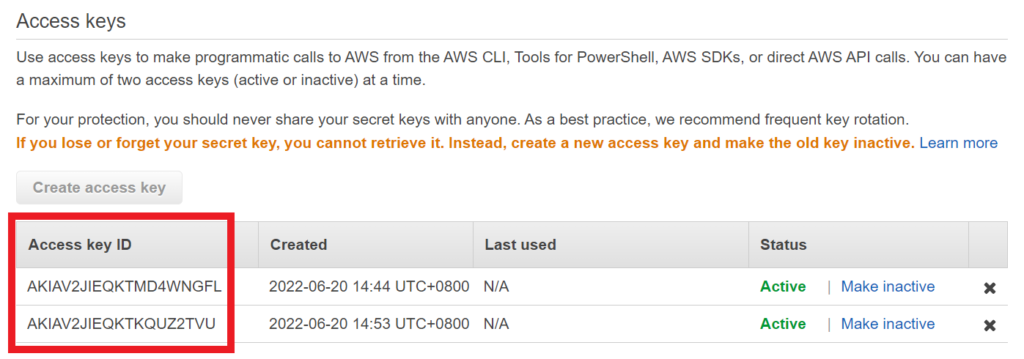
Maximum Number of Access Keys
You can only create a maximum of 2 Access Keys for each IAM user. This is a hard limit so you cannot request AWS to increase it above that number.
Try running the create-access-key command again above to create another Access Key for your IAM User.
If you already have 2 access keys for the IAM user and you run the create-access-key command, then AWS CLI will return an error stating that you cannot exceed the quota of 2 access keys.
An error occurred (LimitExceeded) when calling the CreateAccessKey operation: Cannot exceed quota for AccessKeysPerUser: 2Listing the Access Keys of an IAM User
To list the access keys that are attached to your IAM User, run the command aws iam list-access-keys.
Just like the create-access-key command, it will need the --user-name argument. Change the MyUser to your target IAM User.
aws iam list-access-keys --user-name MyUserSince I already have 2 access keys for MyUser, this will return the following.
{
"AccessKeyMetadata": [
{
"UserName": "MyUser",
"AccessKeyId": "AKIAV2JIEQKTMD4WNGFL",
"Status": "Active",
"CreateDate": "2022-06-20T06:44:30+00:00"
},
{
"UserName": "MyUser",
"AccessKeyId": "AKIAV2JIEQKTKQUZ2TVU",
"Status": "Active",
"CreateDate": "2022-06-20T06:53:41+00:00"
}
]
}Notice that it only returns the AccessKeyId, but it does not show the SecretAccessKey. The SecretAccessKey is like your password, you should be the only one who knows what it is.
Rotate Access Keys
IAM User access keys are what we call permanent access credentials. As a best practice, we must rotate the access keys regularly. What this means is that we must frequently change the access key, because if the access keys are compromised at least it will only be temporarily compromised until the access keys are changed.
Some companies rotate their access keys weekly, some even rotate them daily. It really depends on your company’s requirements. The shorter the period, the better.
Below are AWS CLI commands that will be useful when rotating access keys.
Deactivate Access Key
It is recommended that you do not immediately delete the current access keys, as some of your applications may still need updating. What you can do is deactivate the access key by running the command aws iam update-access-key with the --status argument set to Inactive.
Note: Since an IAM User can have 2 AWS Access Keys, you will need to provide the access key ID in order for the command update-access-key and delete-access-key to know which access key they should change or delete.
aws iam update-access-key --user-name MyUser \
--access-key-id AKIAV2JIEQKTNGPZ3CWH \
--status InactiveReactivate Access Key
In case you need to reactivate the Inactive access keys, you can run the same aws iam update-access-key but the --status argument is set to Active.
aws iam update-access-key --user-name MyUser \
--access-key-id AKIAV2JIEQKTNGPZ3CWH \
--status Active Delete Access Key
If you are sure that your Deactivated key is no longer needed, run the command aws iam delete-access-key.
aws iam delete-access-key --user-name MyUser \
--access-key-id AKIAV2JIEQKTNGPZ3CWHAfter you run this command, the Access Key that you deleted will no longer be accessible or retrievable.
I hope this post helps when you are creating AWS programmatic Access Keys for your IAM User. Let me know your experience in the comments below.